9 Best Ways to Protect your Business from Credential Stuffing
Did you know in 2019, the usernames and passwords of approximately 4 million Canva users were stolen, decrypted, and shared online?
This was a credential stuffing attack.
Confused?
Before moving forward, let’s understand what this term means.
What is a credential stuffing attack?
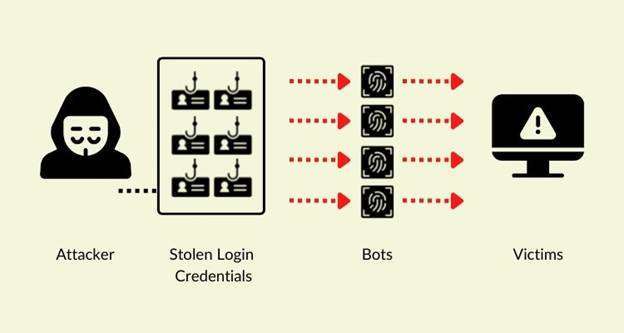
A credential stuffing attack is a cyberattack method in which cybercriminals take over massive databases containing user credentials to breach a system. These criminals use an automated system to access previously breached usernames and password pairs in the website login field.
They try to access the user account on different platforms upon finding the right pair of usernames and passwords.
Image Source: webhostingsecretrevealed.net
These cybercriminals hijack accounts they’re able to log in to.
This technique is increasingly becoming popular as novice hackers have readily available tools to log in to hundreds of online services and websites.
According to research, companies experience an average of 12.7 credential stuffing attacks each month, which causes a loss of a whopping $6 million.
With so much on the table, companies must protect their business from credential-stuffing attacks.
9 best ways to protect your business from credential stuffing
Use these methods to protect your business from potential credential-stuffing crimes:
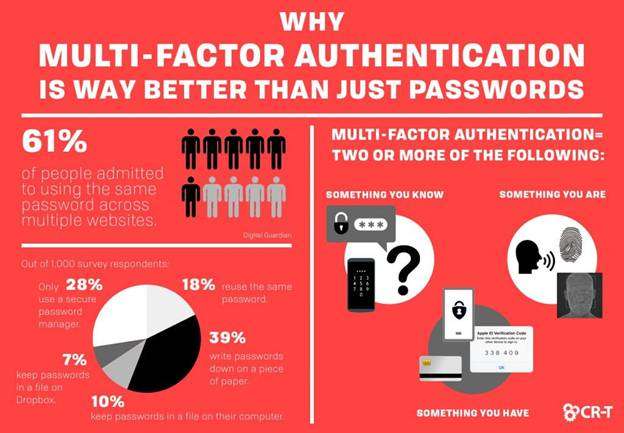
- Use multi-factor authentication during login
To prevent cyber crimes from occurring, use multi-factor authentication (MFA) to allow customers access to your online platforms. The primary objective of using MFA is reducing the risk of account takeover and providing security to customers’ accounts.
Besides asking for the username and password, MFA requires customers to complete one more verification factor, drastically reducing the likelihood of a successful online attack.
Most companies prefer using one-time passwords or OTP, which are 4 to 8 digits codes that you receive on your mobile or email.
Interesting statistics: 61% of customers use the same password on multiple services, making MFA a must for preventing your customer’s account from getting hacked.
- Avoid using email addresses as usernames
As the foundation of credential attacks is people reusing the same username and password, it makes a cybercriminal’s job much easier when your customers use their email address as the username.
Ask users to have different email addresses and usernames, as it decreases the likelihood of customers using the same combination of usernames and passwords on multiple websites.
- Focus on threshold alerting for detecting failed login attempts
It’s a very effective technique for stopping instances of credential stuffing cyberattacks. When a system detects ‘x’ number of failed login attempts, it sends an automated message to the user about the failed attempts and executes a custom script to stop them.
These scripts temporarily disable the login functionality or even shut down the server, preventing the cybercriminal from gaining unsolicited access to a user’s account.
Interesting statistics: In 2020, 3.4 billion credential stuffing attacks affected banks and other financial services.
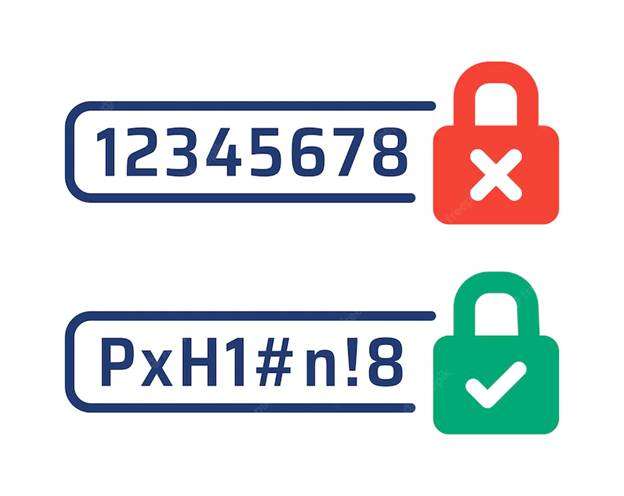
- Have a strong password and authentication policy
One of the easiest and most widely used prevention methods is having a strong password and authentication policy. Encourage customers and employees to use password managers to generate unique and strong passwords.
Teach your employees and customers the benefits of having different passwords for different accounts.
Also, set a strict limit on the number of failed login requests.
For instance, banks allow only 3-5 attempts before temporarily freezing the customer account.
Customers must visit a bank or speak with a customer service associate to unfreeze their accounts.
In addition, encourage your employees and customers to reset their passwords regularly.
Interestingly, 81% of data breaches occur as customers use a weak password or otherwise compromised credentials for logging in to their accounts.
- Adopt passwordless authentication
Many companies are using a new and innovative way to prevent credential stuffing cyberattacks – passwordless authentication.
Instead of using a password to identify a customer, passwordless authentication verifies a customer using their device, another account, or biometrics.
Passwordless authentication takes your sign-in security from better to the best. It eliminates the potential theft of passwords.
Such methods save your customers from the hassle of remembering long and complex passwords.
Interesting statistics: 78% of Gen-Z customers use the same password for several online accounts.
- Use a web application firewall (WAF)
Implementing a web application firewall is an excellent way of detecting abnormal traffic from cyber criminals.
Most WAFs identify potential login attempts, especially when cybercriminals suddenly try many attempts.
Apart from identifying potential credential stuffing instances, WAF prevents data breaches caused during a web attack.
Pro-tip: Implement WAF on all your websites to prevent data breaches and credential stuffing.
- Use credential hashing
To prevent cyber criminals from stealing passwords, use credential hashing. In the credential hashing process, the system scrambles a user’s password before storing it in your database. Even if cybercriminals get access to these passwords, they won’t be able to use them.
Though hashing passwords might be too effective in preventing credential stuffing, it helps limit what cybercriminals can do with those stolen passwords.
Pro-tip: Credential hacking differs from encryption as it is a one-way cryptographic function, while encryption works both ways. As the encryption process is reversible,
cybercriminals obtain the secret key to decrypt the text.
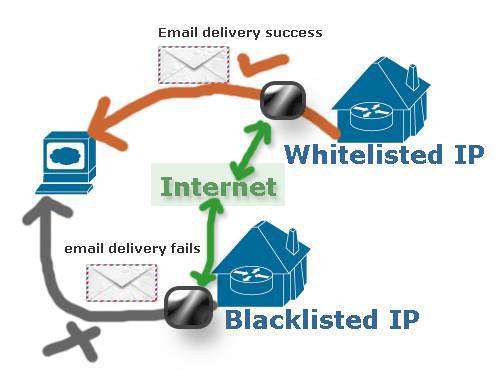
- Use IP blacklisting
Usually, cybercriminals have access to a limited pool of IP addresses. When you notice login attempts to multiple accounts from the same IP address, blacklist all such IP addresses.
To avoid falling prey to false positives, keep track of the last several IP addresses used to login into your customer’s account. Then, compare IP addresses to the suspicious ones.
The only downside of using IP backlisting is that cybercriminals might use techniques such as IP spoofing, which gives an impression that they’re connecting to the system using a different IP address.
This allows cybercriminals to bypass blacklisting while obscuring their identity.
Pro-tip: A comprehensive IP blacklisting process prevents cybercriminals from stealing credentials and gaining access to your customer’s credentials.
- Block the use of headless browsers
A headless browser is a web browser without a user interface. Though these browsers access the webpage, the graphical user interface or GUI is hidden from users.
Typically, developers use headless browsers for website and application testing and JavaScript library testing, but cybercriminals use them for click frauds and to gain access to customers’ credentials.
Blocking access to these headless browsers means preventing suspicious activities.
Pro-tip: As these browsers don’t have a GUI to navigate, you control or block such browsers using automated scripts or a command-line interface.
Examples of credential stuffing attacks
Since its inception, credential stuffing attacks have impacted businesses in every sector. Some prominent and noteworthy attacks are:
The North Face
The North Face, a well-known outdoor retailer, faced a massive credential stuffing attack in 2020. The attackers got access to information, such as customers’ names, phone numbers, billings, shipping addresses, email preferences, and favorite goods.
After the attack, North Face had to reset passwords for an undetermined number of customers. Also, the company reduced the account login rate from any suspect source.
HSBC
Towards the end of 2018, HSBC faced a major credential stuffing attack, which compromised the financial security of thousands of customers.
The bank suspended access to online accounts for all impacted customers and started procedures for changing passwords for online banking accounts. The bank eventually applied various cybersecurity measures to prevent future attacks from occurring.
DailyMotion
In 2019, DailyMotion encountered a large-scale and ongoing credential-stuffing assault by cybercriminals. The video-sharing platform alerted all its impacted customers and provided personalized support to each of them.
Dunkin Donuts
In three months, Dunkin Donuts became a victim of a credential stuffing attack twice. The attackers gained access to their customer’s first name, last name, email address, and 16-digit Dunkin Donuts account number and the perks QR code. Dunkin Donuts actively notified customers about this attack.
The company used various measures to prevent further attacks and ensured the security of customers’ details.
Preventing credential stuffing attacks like a pro
While there is no definitive solution for preventing credential stuffing cyberattacks, following the measures mentioned above provides an extra layer of security.
Cybercriminals and your customers use the same browsers, so your business requires solid and efficient credential-stuffing protection to detect potential attacks.
Irrespective of whether you’re a small or medium-sized business, it’s imperative to have a reputable security partner that helps you achieve your security requirements and ensure your customer’s credentials remain in safe hands.
Leave no stone unturned when implementing these nine tips, as it’s your business and your customers, and you must protect their credentials.